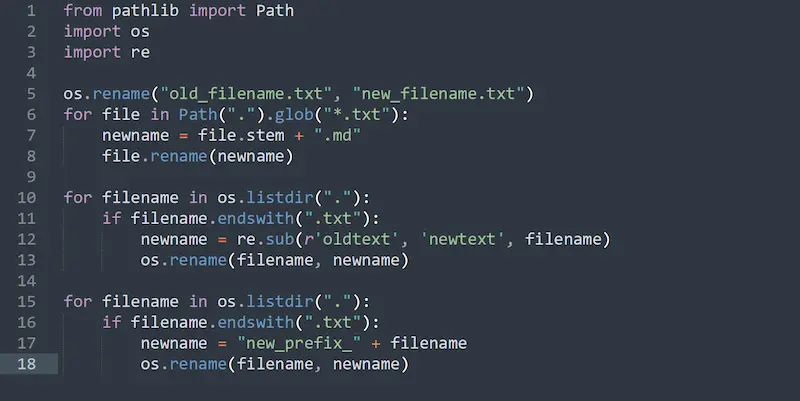
Renaming multiple files at once is a common task for IT professionals, developers, and anyone who works with large numbers of files. Whether you’re organizing a batch of photos, updating file extensions, or reformatting filenames to fit a specific pattern, automating the renaming process can save significant time and reduce errors. This article will explore how to rename multiple files using two powerful scripting tools: Bash and Python.More
Understanding SIEM: Security Information and Event Management
In today’s digital landscape, where cybersecurity threats are increasingly sophisticated, organizations need robust tools to protect their networks and data. Security Information and Event Management (SIEM) solutions are a cornerstone of modern cybersecurity strategies. This article explores what SIEM is, its uses, how to configure it, and its common features.More
Understanding Spanning Tree Protocol (STP): Ensuring Network Stability and Efficiency
In modern enterprise networks, maintaining stability and efficiency is crucial, especially in environments with multiple interconnected switches. The Spanning Tree Protocol (STP) is a key technology that helps prevent network loops, ensuring that your network remains operational and efficient. This article explores how STP works, why it’s necessary, the problems it solves, how to configure it, and the common configuration options available.More
Essential Linux Commands and Bash Scripting for IT Administrators: A Quick Guide
Linux is a powerful and flexible operating system widely used in enterprise environments, especially for servers and network management. For IT administrators, mastering the basic Linux commands and Bash scripting is essential for managing systems effectively, analyzing issues, and quickly resolving problems. This article covers key Linux commands, their usage, and how Bash scripting can streamline your work as an IT administrator.More
Understanding Horizontal and Vertical Scaling in Azure: A Guide to Scalability
In the cloud computing world, scalability is a critical concept that refers to the ability of a system to handle increased load. Microsoft Azure, one of the leading cloud platforms, offers robust scalability options, allowing businesses to efficiently manage their resources as demand fluctuates. Two primary methods of scaling are horizontal scaling and vertical scaling. This article will explore these concepts in the context of Azure, highlighting how they work, their advantages and disadvantages, and when to use each type to optimize your cloud infrastructure.More
Understanding RAID: Types, Advantages, Disadvantages, and Use Cases
Redundant Array of Independent Disks, or RAID, is a technology used to improve the performance, data security, and fault tolerance of storage systems. By combining multiple physical drives into a single logical unit, RAID allows you to achieve various benefits depending on the RAID level used. In this article, we’ll explore the most common RAID levels—RAID 0, 1, 5, and 10—discuss their advantages and disadvantages, and provide guidance on when to use each type. We’ll also touch on the importance of RAID in maintaining data security and integrity.More